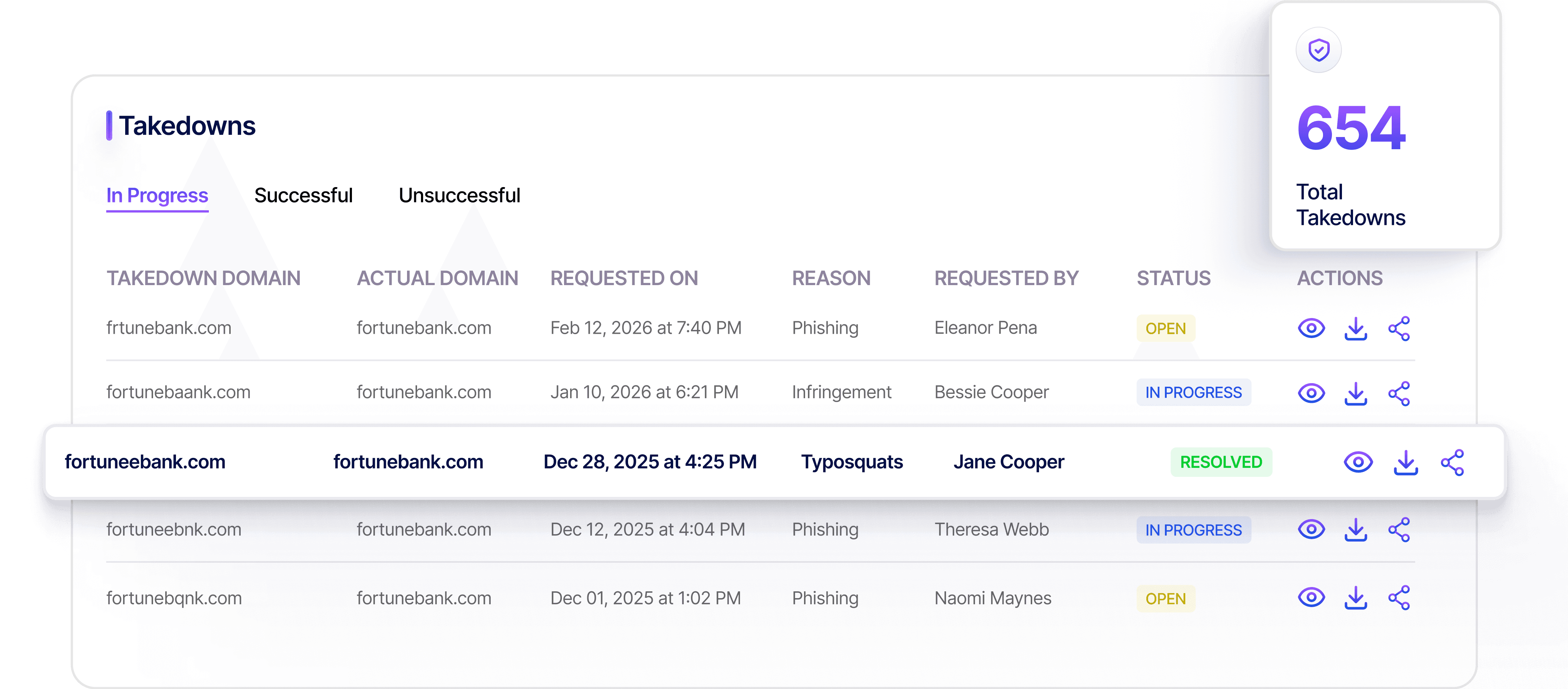
Takedown Brand Threats Faster with Agentic AI
Enable Threat Disruption and
Takedown Management at
scale with
KnyX AI
Modern threats do not stop at detection. KnyX AI autonomously validates abuse, maps ownership, hosting dependencies, and executes takedown workflows across registrars, hosting providers, social platforms, app stores, and content delivery networks.
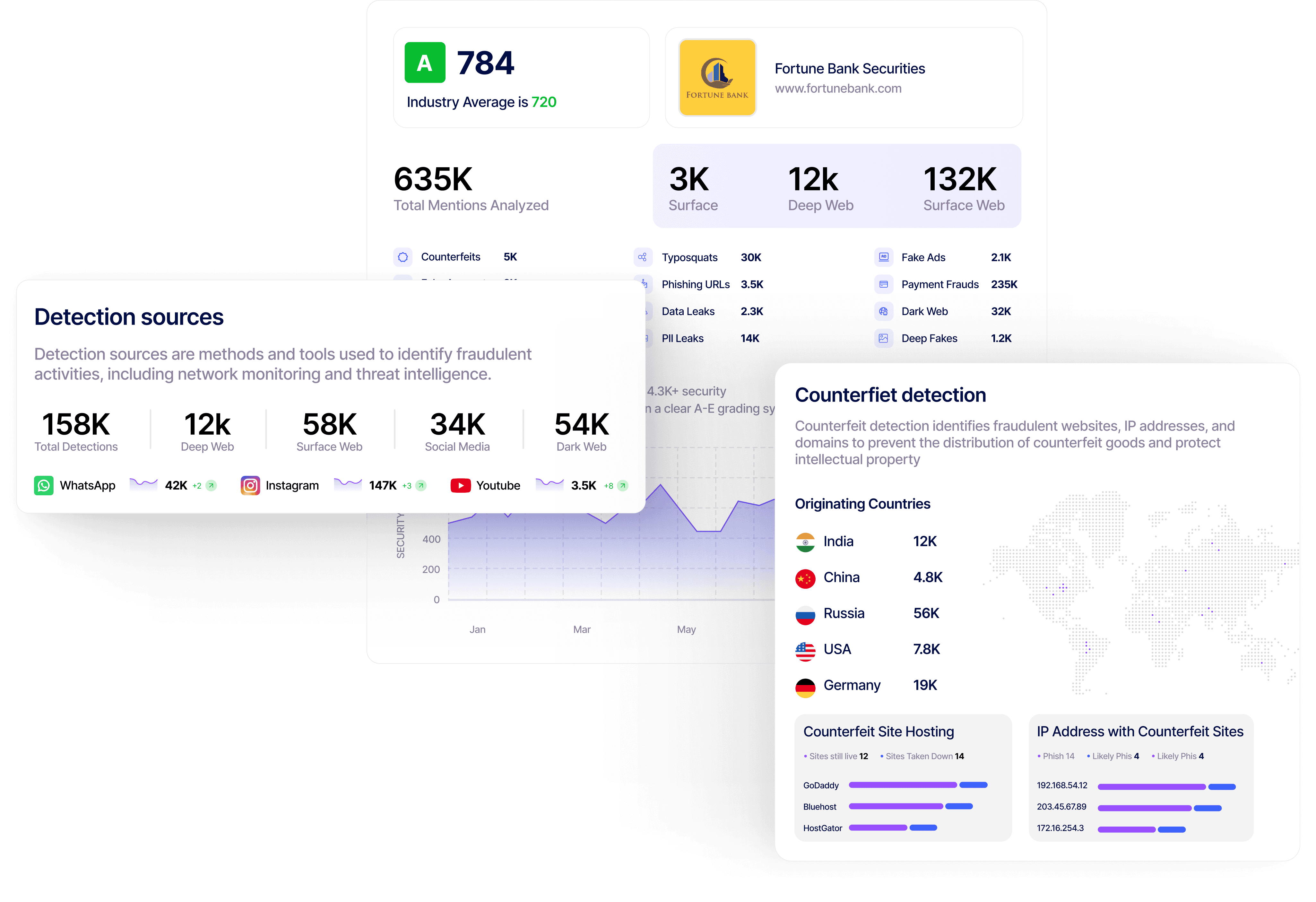
Streamlining
Takedown Management with KnyX AI
Transform chaos into clarity with RiskProfiler’s intelligent reasoning layer
Scale Domain Takedown Workflows with KnyX AI
Validate and disrupt malicious domains and impersonation campaigns using contextual agentic AI-powered workflows

Lookalike Domain Detection
Continuously monitor new registrations, DNS changes, and infrastructure reuse to surface typosquats early and reduce customer exposure before campaigns scale.
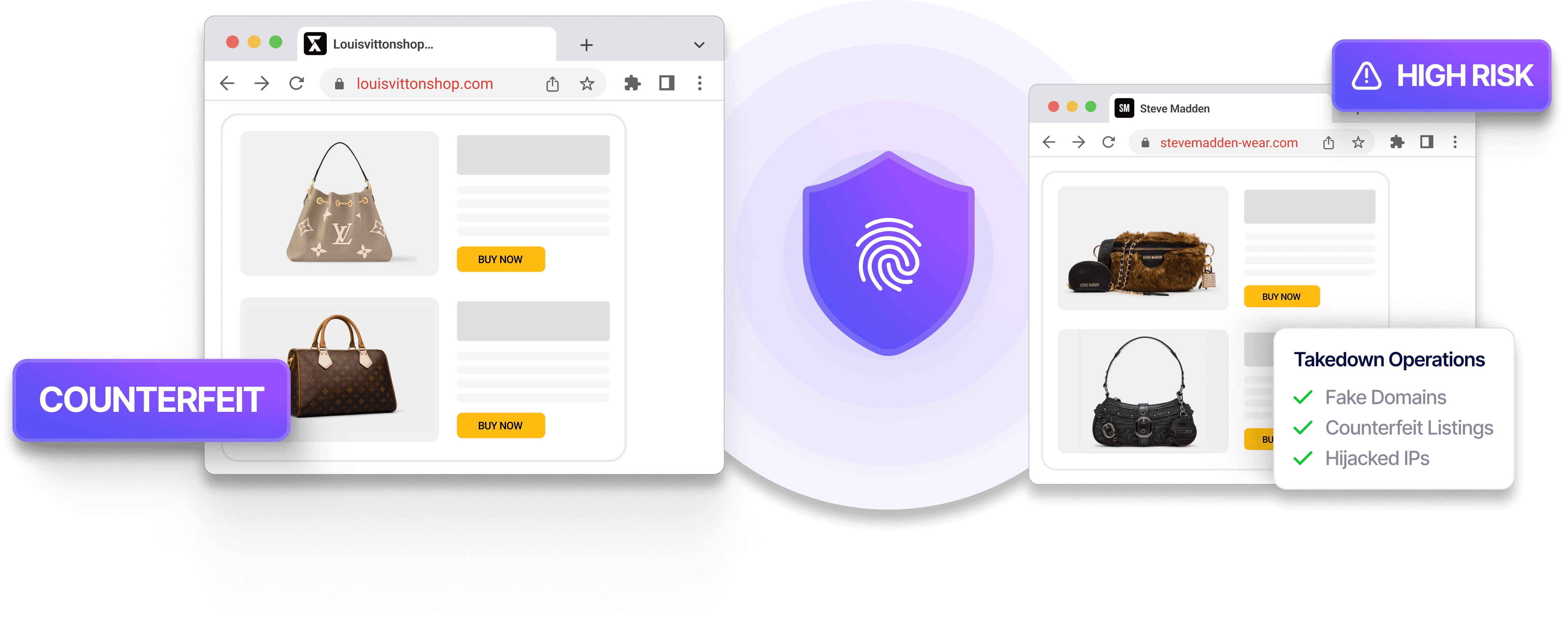
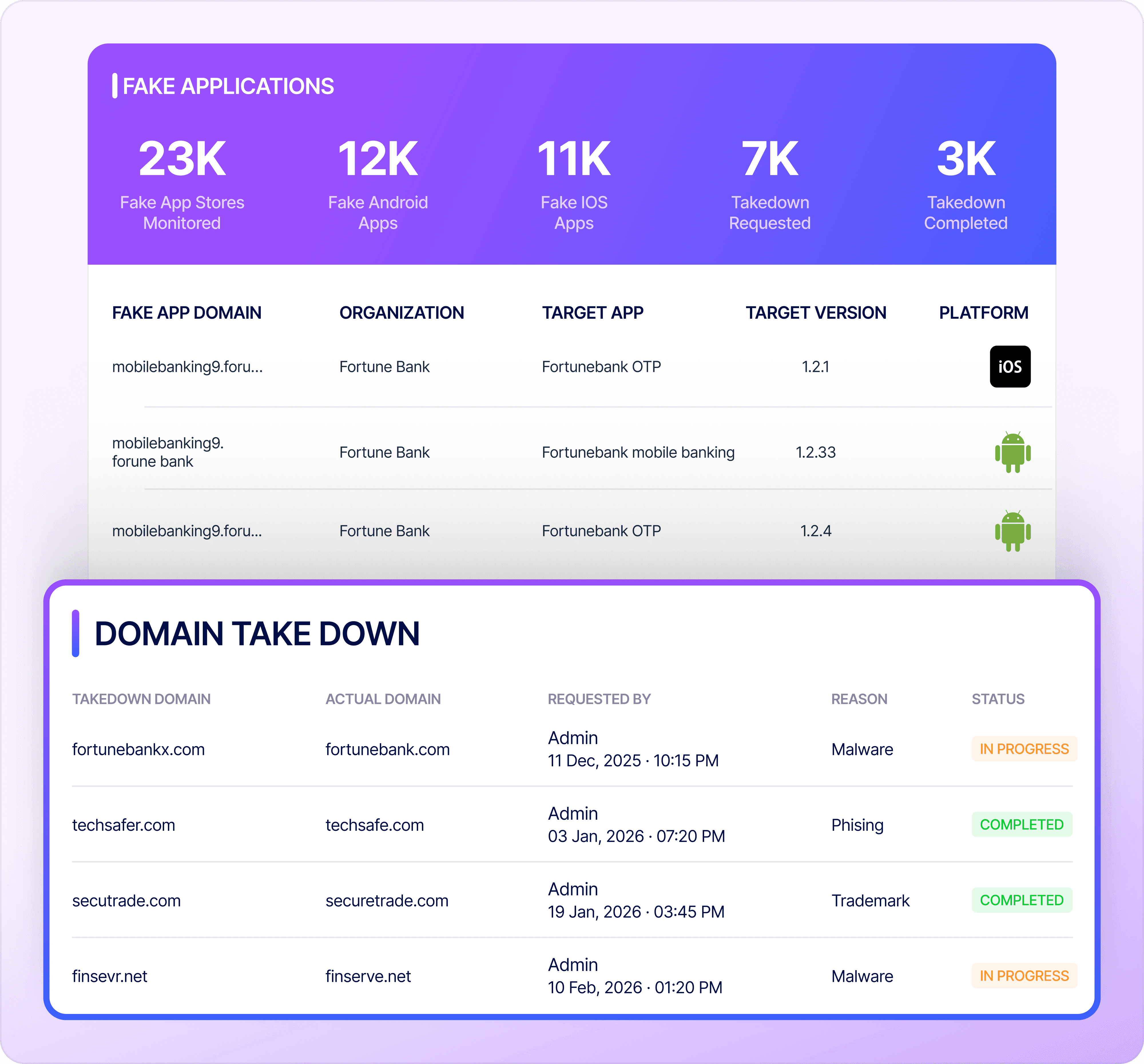
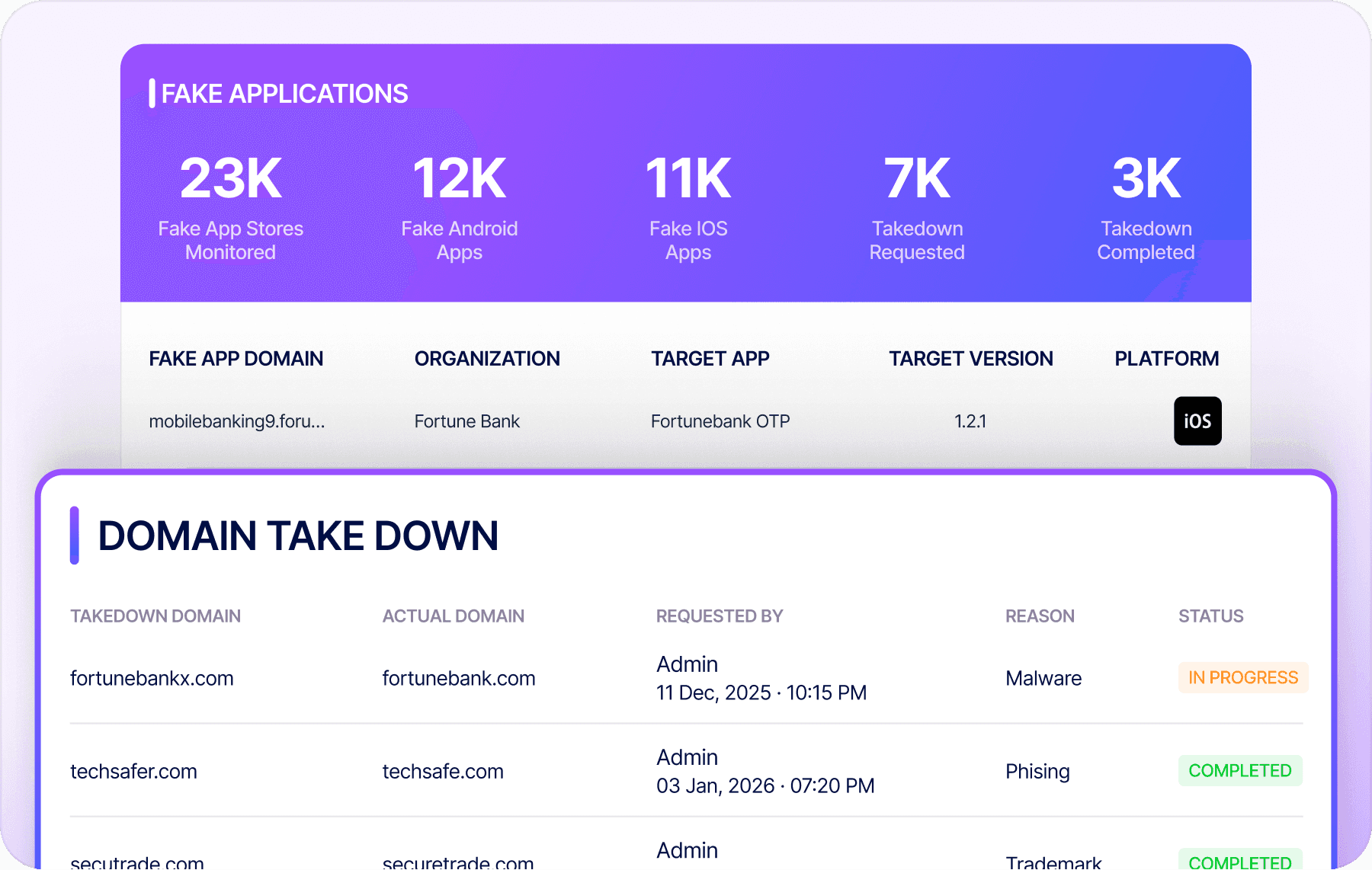
Streamline Spoofed Domain Takedowns
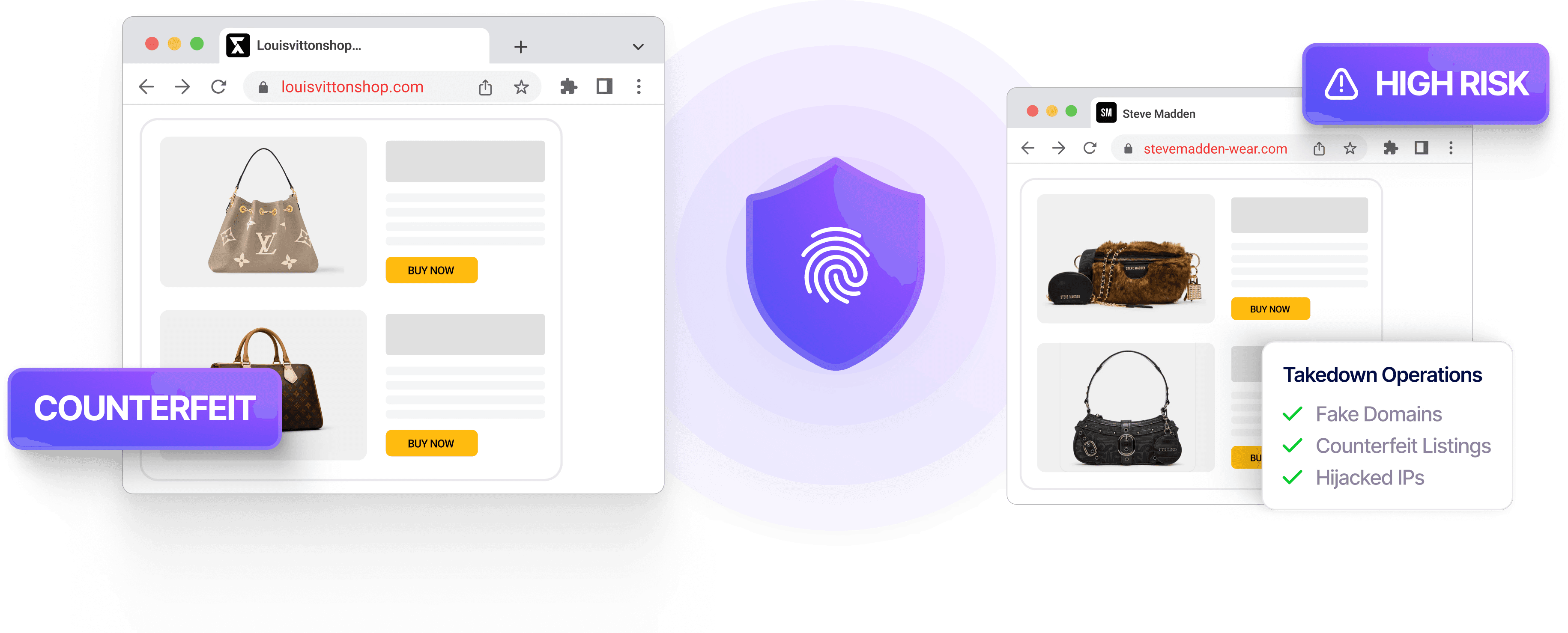
Detect and remove lookalike, impersonating, and counterfeit domains used for phishing and brand fraud, backed by evidence, end-to-end tracking, and audit-ready reporting.

Prevent Abuse of Copyrighted Assets
Identify and disrupt unauthorized use of logos, brand assets, and digital content across websites, social platforms, marketplaces, and ads, using AI-powered takedown workflows to stop abuse at scale.

Correlate Breach Exposure Intelligence
Correlate leaked credentials and breach artifacts to domains, executives, and social identities to prioritize remediation, reduce takeover risk, and disrupt impersonation attempts.
End-to-End Threat Disruption and
Takedown Management
Continuously detect and remove high-impact digital abuse and brand threats across channels to protect revenue, reputation, and customer trust.
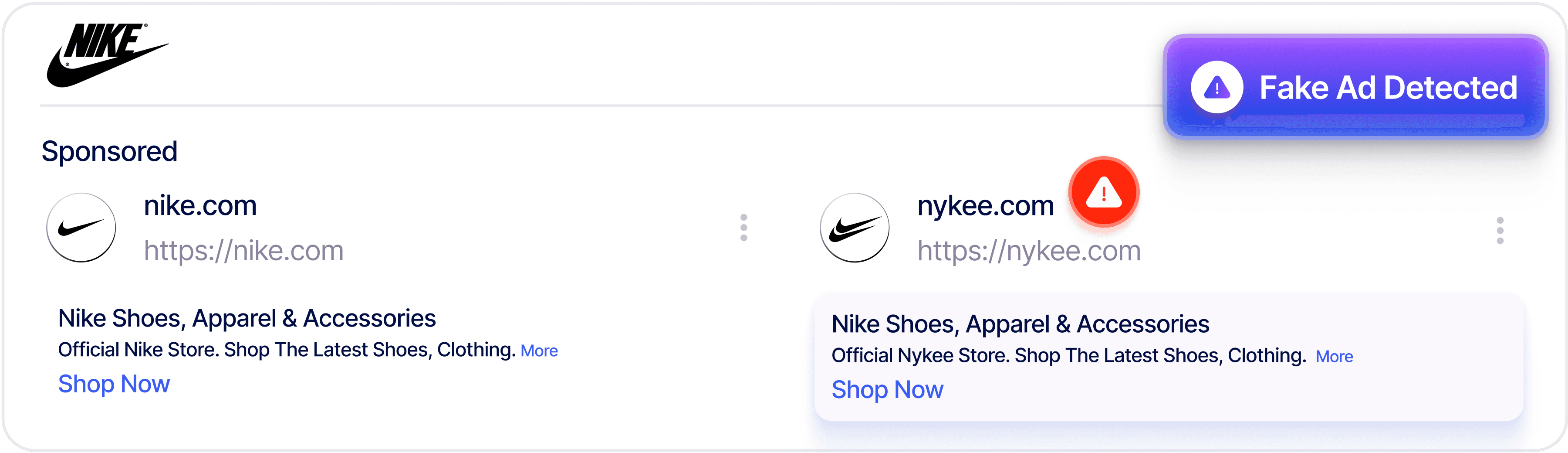
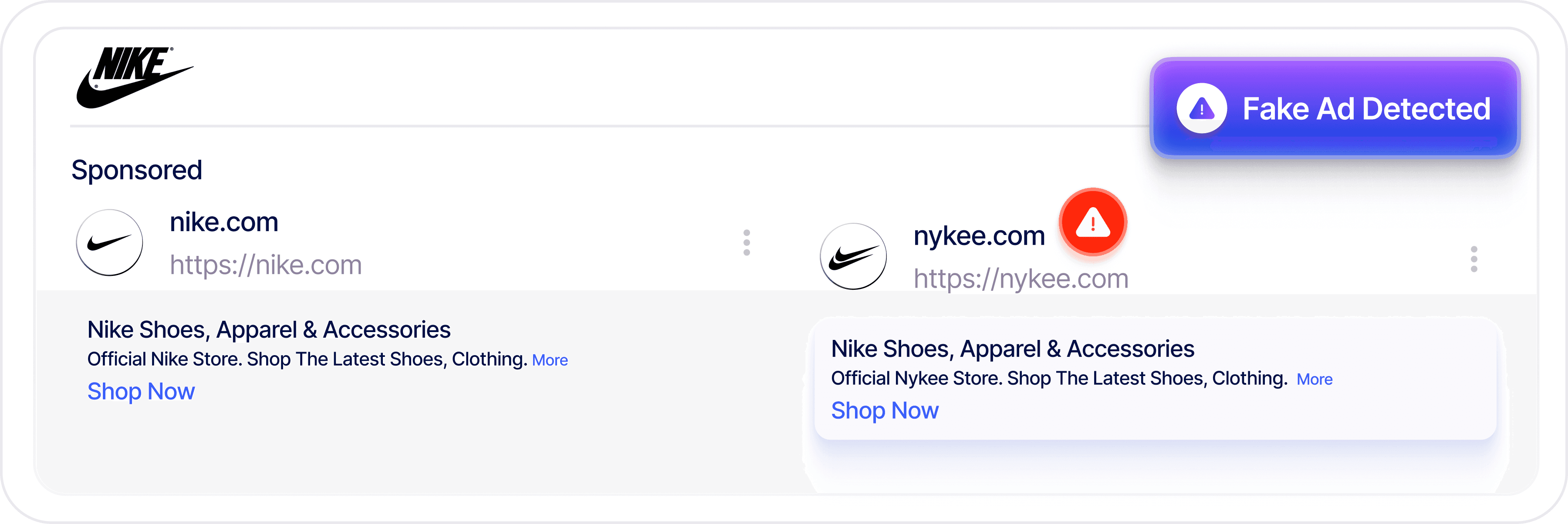
Scam & Malicious Ad Takedown
Detect and remove fraudulent ads, scams, and malicious online posts that misuse your brand to deceive customers, distribute malware, or drive financial fraud across networks.
Remove Counterfeit Product Listings
Identify and take down fake product listings across e-commerce platforms and marketplaces to protect revenue, brand integrity, and customer trust.
Misinformation Takedown
Track and eliminate false narratives, coordinated misinformation, and defamatory content targeting your organization or executives.

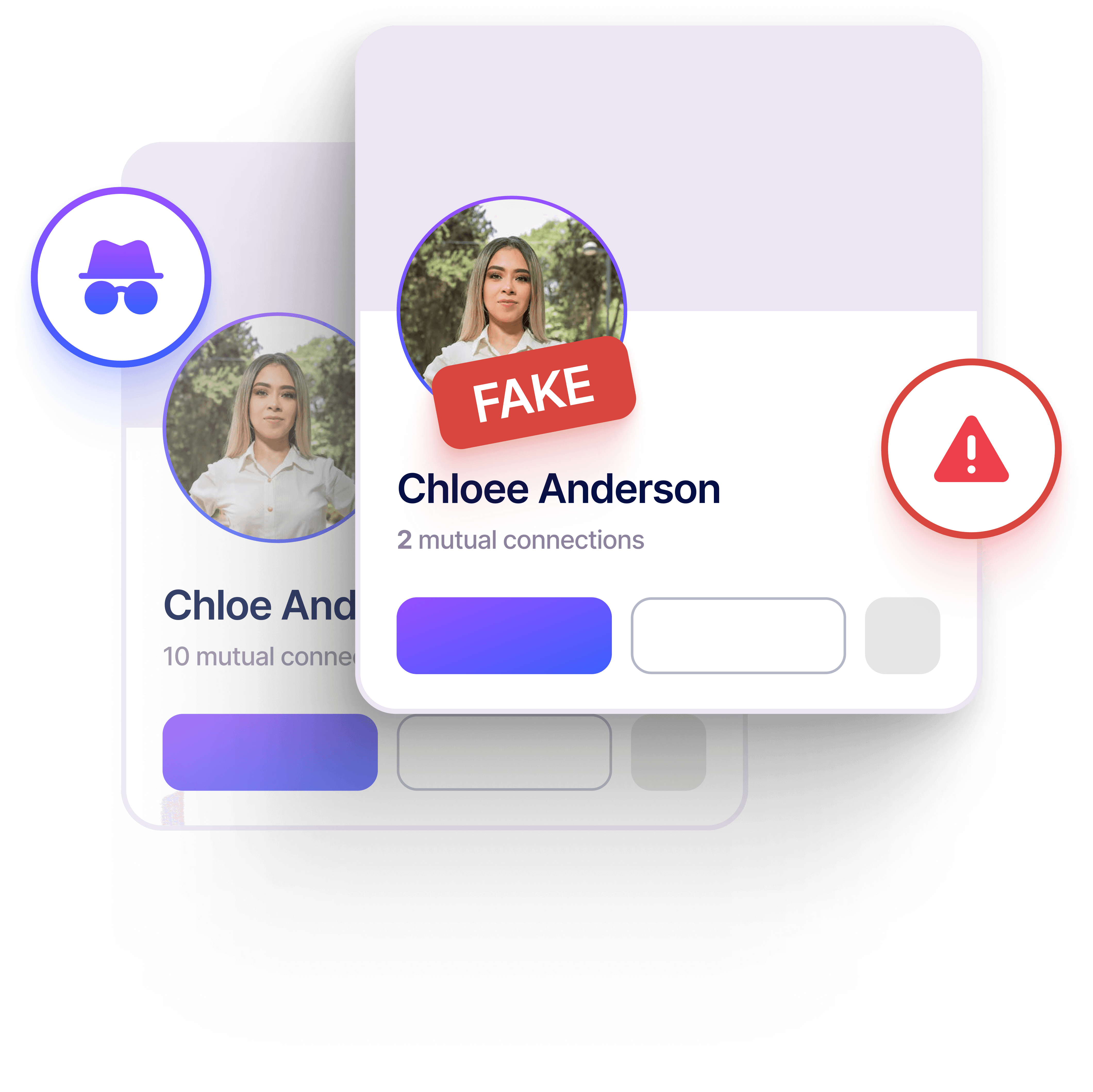
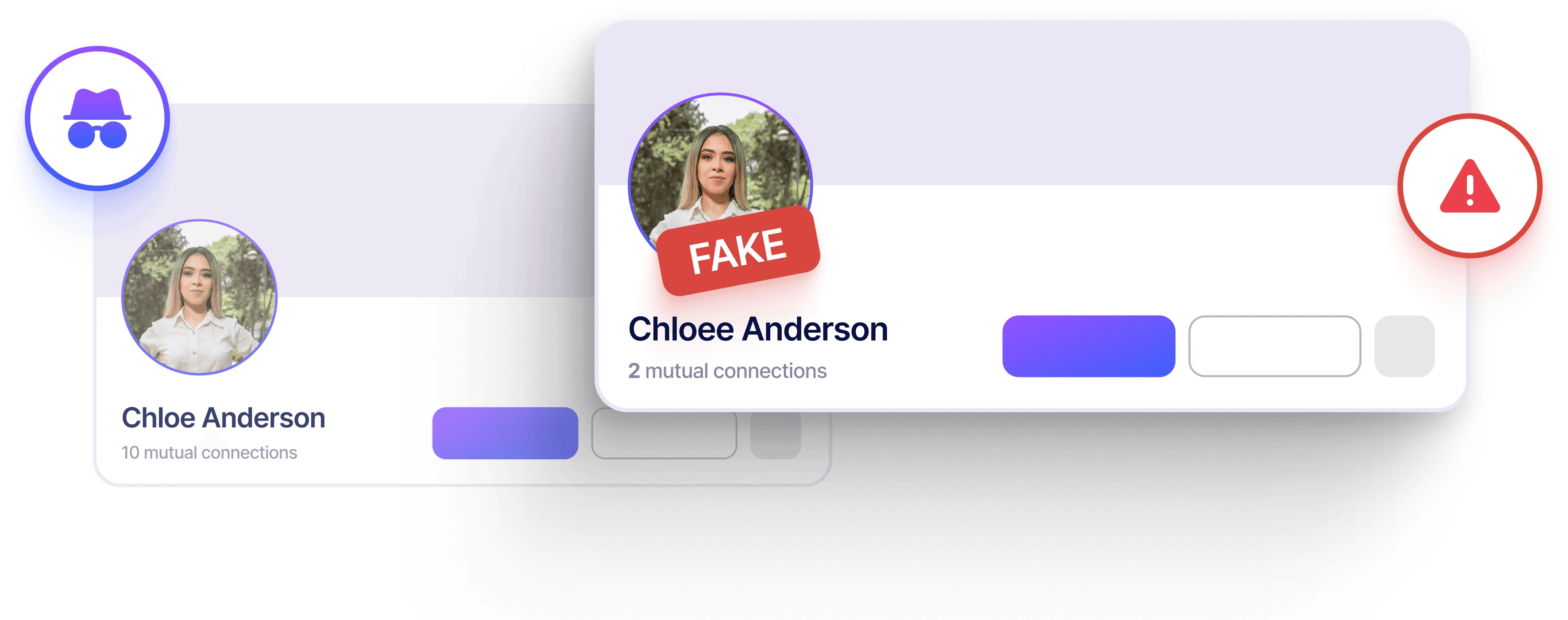
Social Media Impersonations
Detect and remove fake profiles, executive impersonations, and malicious content on social platforms to prevent fraud, misinformation, and reputational damage.
Why Choose RiskProfiler
Takedown Management?
Enabling takedown management to operate as an intelligent system, not a reactive process.

1
AI-Powered Prioritization and Action
KnyX AI evaluates intent, exposure, and impact to prioritize high-risk abuse and automate takedown execution, reducing manual effort while maintaining control and accuracy.

2
Verified Takedown Execution
RiskProfiler validates threat signals using contextual intelligence and platform-ready evidence for takedown actions. KnyX Brand AI streamlines verification and routing, ensuring end-to-end consistency and traceability.

3
Protection Against Re-Emergence
Continuous agentic AI-powered monitoring detects re-registrations, mirror sites, and repeat abuse patterns, preventing attackers from resurfacing after initial takedown.
Trusted by
Security Leaders

4.8/5

4.8 out of 5 stars

Best Ease of Use
2024
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Got Questions?
We Have Answers!
What it is, how it works, and why digital and physical security must operate together.
What is RiskProfiler’s Takedown Management solution?
RiskProfiler’s Takedown Management solution goes beyond basic threat detection by validating abuse using contextual intelligence, mapping domain ownership and hosting dependencies, and executing end-to-end takedown workflows. Powered by agentic AI, it generates platform-ready evidence, coordinates directly with registrars, hosting providers, social platforms, app stores, and CDNs, and tracks execution status until resolution, ensuring threats are not just identified, but fully removed.
How quickly can phishing and malicious domains be taken down using RiskProfiler?
By automating validation, evidence preparation, and registrar or hosting coordination, RiskProfiler enables phishing, brand spoofing, and malicious domain takedowns to be initiated in hours instead of days, significantly reducing customer exposure and fraud risk.
Can RiskProfiler handle fake app and social media impersonation takedowns?
Yes. RiskProfiler monitors fake Android and iOS apps across app stores, validates impersonation or abuse on social media networks, and manages takedown execution workflows to protect customers from malicious or fraudulent mobile applications, targeted harassment, and identity fraud.
How does RiskProfiler prevent threats from re-emerging after a takedown?
Continuous agentic AI-powered monitoring detects mirror sites, re-registrations, infrastructure reuse, and repeat abuse patterns, enabling proactive disruption before attackers can relaunch phishing or brand abuse campaigns.

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.










© 2026 RiskProfiler | All Rights Reserved
Take a Product Tour
Trusted by
Industry Leaders


4.8/5


4.8 out of 5 stars


Spot Typosquat Domain
Detect typosquats early via domain, DNS, and infrastructure monitoring.
Streamlined
Takedown
Takedown lookalike and counterfeit domains at scale, retaining brand trust
Prevent Copyright Abuse
Detect and disrupt misuse of brand logo, creatives, and copyrighted assets at scale, with streamlined workflows
Features
End-to-End
Physical
Intelligence
Security
Features
End-to-End Threat Disruption
and Takedown Management

Scam & Malicious Ad Takedown
Detect and remove fraudulent ads, scams, and malicious online posts that misuse your brand to deceive customers, distribute malware, or drive financial fraud across networks.

Remove Counterfeit Product Listings
Identify and takedown fake product listings across e-commerce platforms and marketplaces to protect revenue, brand integrity, and customer trust.

Social Media Impersonations
Detect and remove fake profiles, executive impersonations, and malicious content on social platforms to prevent fraud, misinformation, and reputational damage.

AI-Powered Prioritization and Action
Automated intelligence accelerates high-risk takedowns with full oversight.


Verified Takedown Execution
Contextual intelligence validates threats, enabling KnyX Brand AI in traceable takedowns.


Protection Against Re-Emergence
Continuous AI monitoring prevents re-registrations, mirror sites, and recurrences.


Benefits
Why Choose RiskProfiler
Takedown Management










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved
Trusted by
Security Leaders
See what real users are saying about RiskProfiler. We don't filter. We just ship.


4.8/5


4.8 out of 5 stars
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
Voices of Security Leaders
Takedown Brand Threats Faster with Agentic AI
Threat Disruption and Takedown Management
Enable at scale with KnyX AI
KnyX AI autonomously validates abuse, maps ownership, and executes takedown workflows across registrars, hosting providers, social platforms, app stores, and content delivery networks.


Trusted by 500+ enterprises
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.


















































